To disable Root account in AWS Organization member accounts is a good security practice. However, keep in mind that it’s important to ensure that you have alternative means of accessing and managing those accounts before disabling the root account.
Service Control Policies (SCP)
Service Control Policies (SCPs) in AWS Organizations are used to set fine-grained permissions for member accounts within an organization. To restrict all root access to member accounts, you can create an SCP that denies the necessary permissions.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "RestrictAccessForRoot",
"Effect": "Deny",
"Action": [
"*"
],
"Resource": [
"*"
],
"Condition": {
"StringLike": {
"aws:PrincipalArn": [
"arn:aws:iam::*:root"
]
}
}
}
]
}Sign in to the AWS Management Console:
- Open the AWS Organizations console at https://console.aws.amazon.com/organizations/.
- Sign in with your AWS account credentials.
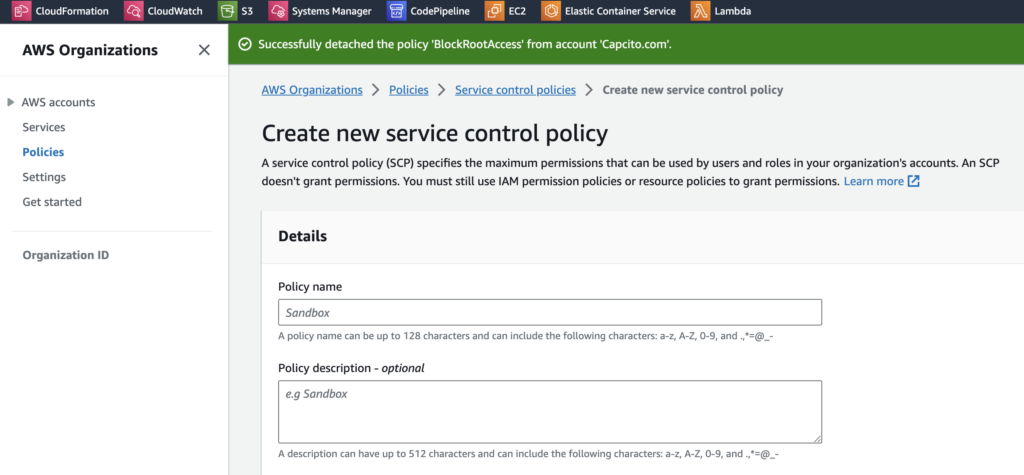
Create a new SCP:
- In the left navigation pane, choose “Policies.”
- Choose the “Create policy” button.
- Enter a name and description for the policy.
- In the “Policy content” section, paste the JSON policy mentioned above.
- Choose the “Create policy” button.
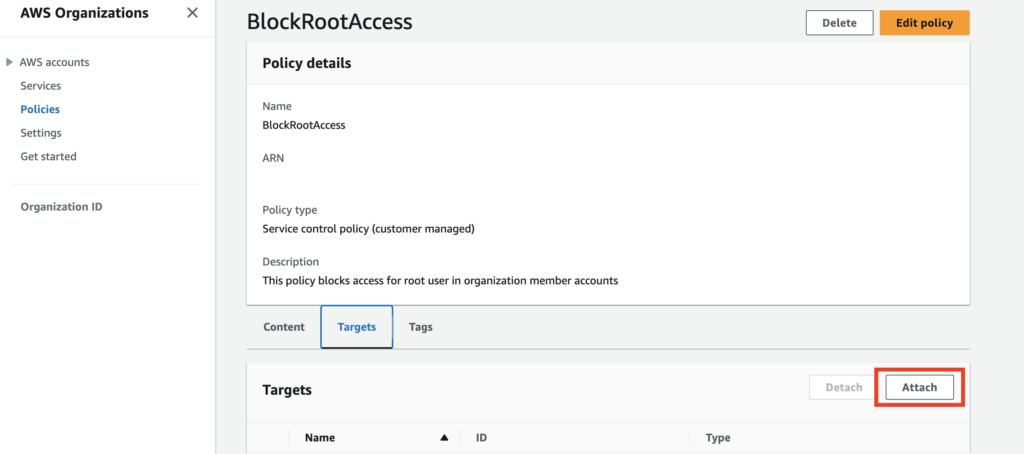
Attach the SCP to your organization:
- In the AWS Organizations console, choose “Policies” in the left navigation pane.
- Select the policy you just created.
- Choose the “Attach policy” button.
- Select the root of your organization and choose “Attach policy.”
After these steps, the SCP will take effect, and it will deny all actions for the root user in all member accounts of your organization. Make sure to carefully test the policy in a safe environment before applying it to a production AWS Organization. Additionally, always have a plan for managing access and troubleshooting in case any issues arise.
If you don’t want to disable root account in your master account, then do not apply it to your whole organization but rather to individual organizational units.

